As true for corporate networks as for broadcast networks, security needs to underpin everything we do to ensure the smooth running of service, that ransomware is kept out and that our data is kept in. This doesn’t mean every device has to have every security feature turned up to 11, it means that security – and which threats need to be protected against – have been thought through at the system level.
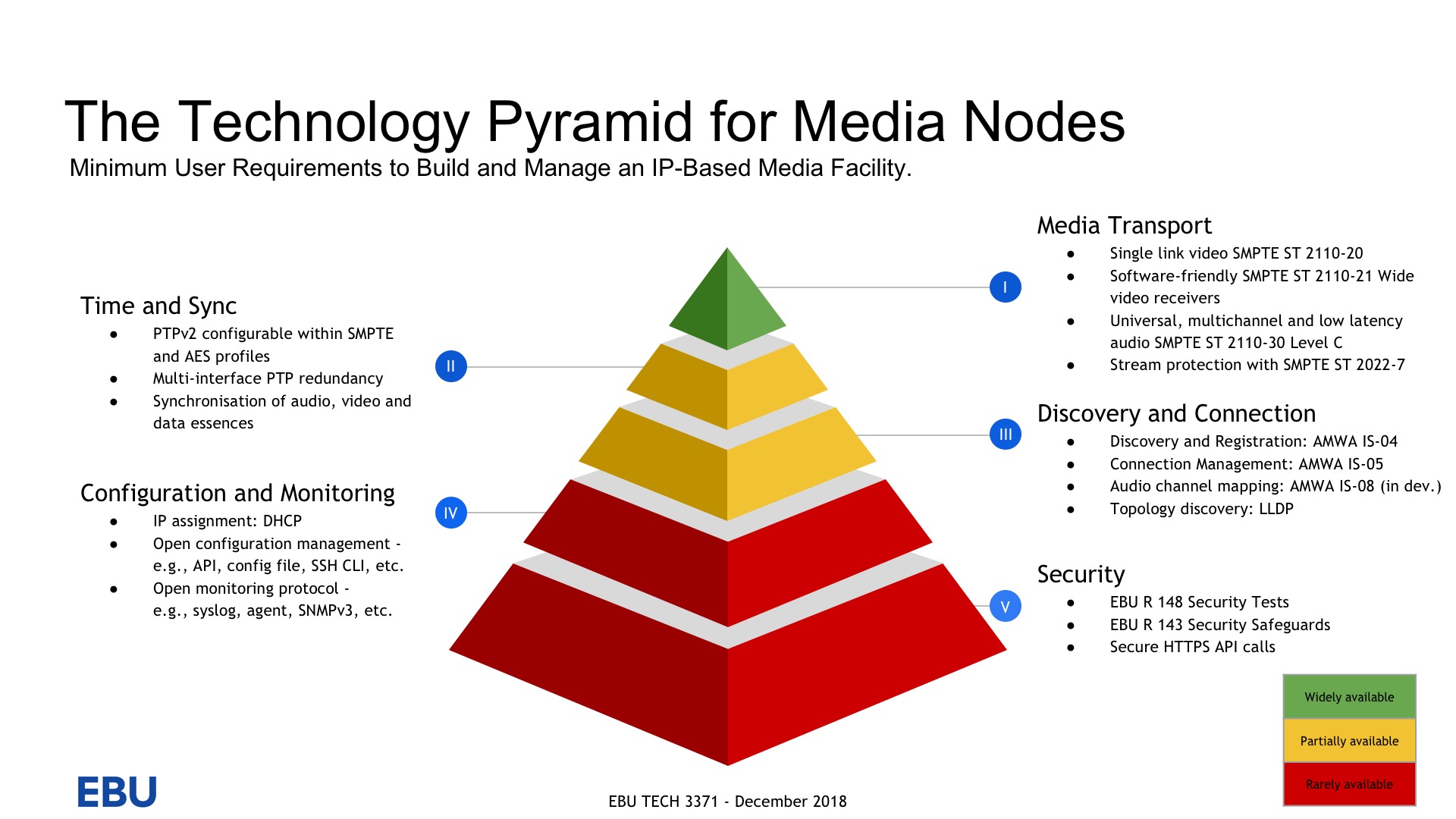
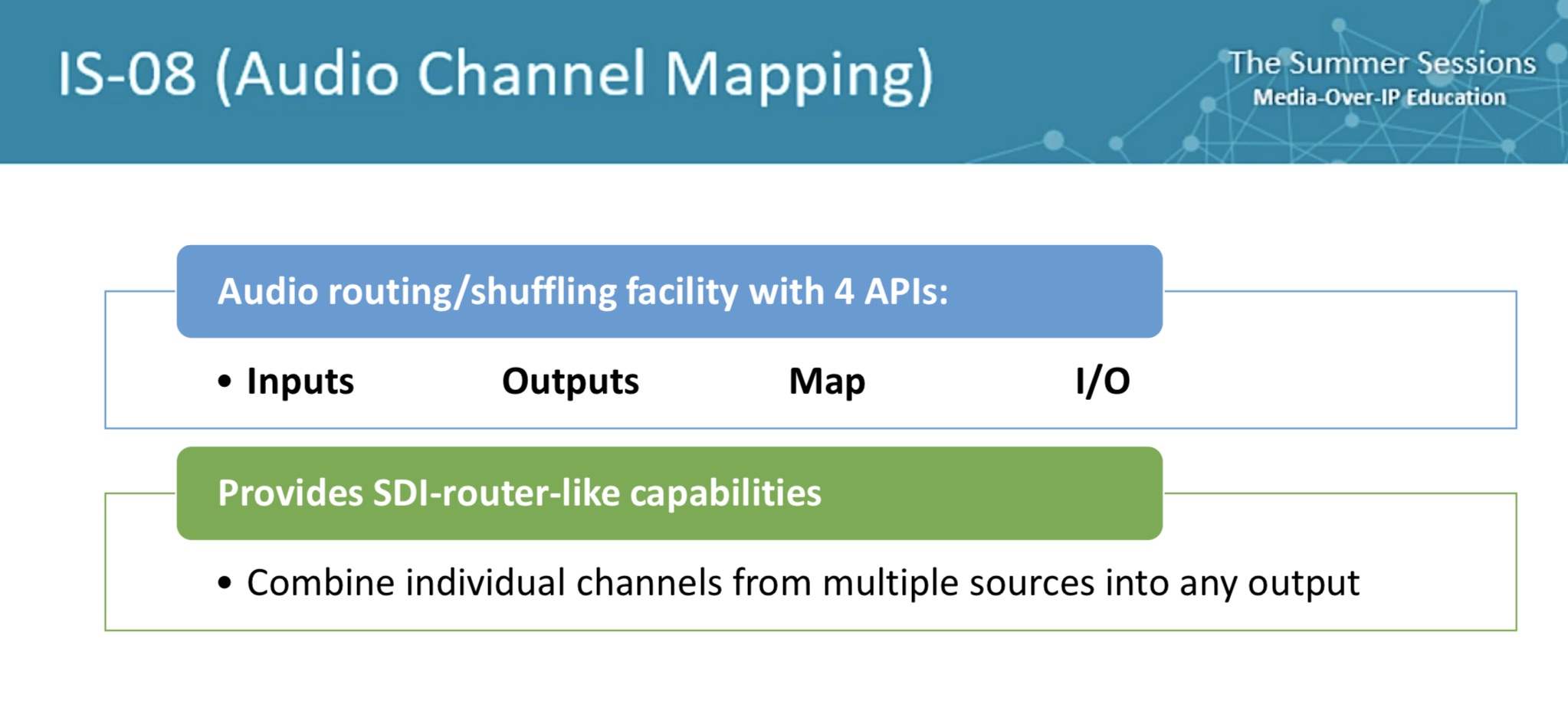
Such importance has security in broadcast facilities, that we see it as the foundational layer of the EBU’s Technology Pyramid. We see SMPTE ST 2110 at the top and whilst this is seen as the ‘business end’, it’s not practical without all that underpins it; the system timing, the NMOS protocols and the security practices.
In this video, Ray Scites explains the threats to networks and challenges the audience to take them seriously showing how mitigations can be implemented. He explains some of the common attacks on networks, both technical and human. Human attacks are phishing attacks which effectively simply ask for the details. Starting with asking for seemingly innocuous information like “Is Donald available today?” and building on knowing that someone is away to put on pressure to hand over information “Donald told me this needs doing right now or the $1,000 deposit will be lost.” With enough small information providing the context, people can be tricked into thinking that an attacker is legitimately doing business and their requests complied with.
To supplement the human element, vulnerabilities can be used. Ray highlights that it’s not just Windows 10 that needs updates, the CVE list of vulnerabilities shows that just this year over 40 security issues with Netgear devices have been publicly reported; all elements in the network need to be kept up to date.
Ray looks at the levels of firewall available from the basic features such as port blocking and forwarding to advanced, like intrusion detection and deep-packet-inspection. The latter technology being where packets are not just forwarded, but read to determine their payload and make firewall decisions based upon the contents. He then explains how port forwarding and NAT (Network Address Translation) work in firewalls.
The cloud offloads all the functionality, but none of the liability.
Ray finishes by showing a brute-force password attack in real time and answering questions covering how to implement security around hardware devices which had no security features, using remote PC terminals to maintain security and whether attacks are on the increase.
Watch now!
Speaker
 |
Ray Scites KNL Consulting Services |