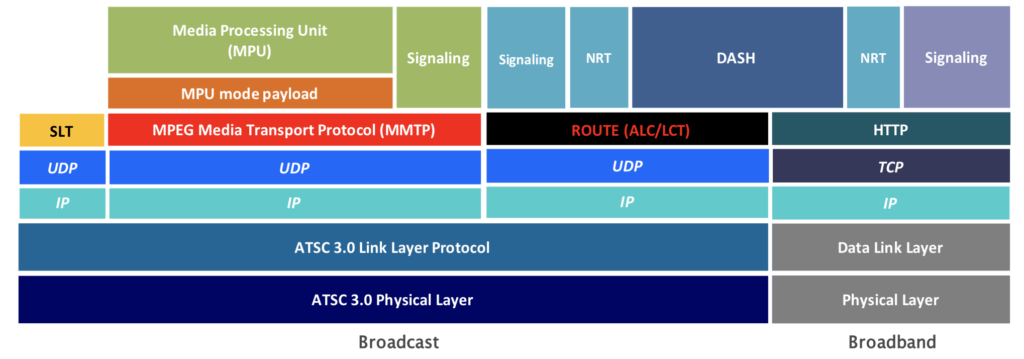
ATSC 3.0 brings IP delivery to over-the-air TV marking a major change in delivery to the home. For the first time video, audio and other data is all delivered as network streams allowing services available to TV viewers at home to modernise and merge with online streaming services better matching the viewing habits of today. ATSC 3.0 deployments are starting in the USA and it has already been rolled out in South Korea for the XXIII Olympic Winter Games in 2018.
Whilst the move to IP is transformational, ATSC 3.0 delivers a whole slew of improvements to the ATSC standard for RF, bandwidth, Codecs and more. In this, the first of three webinars from the IEEE BTS focussing in on ATSC 3.0, we look at the physical layer with Luke Fay, Chair of the ATSC 3.0 group and also a Senior Manager of Technical Standards at Sony.
Click to register: Wednesday, 15th January, 2020. 11am ET / 16:00 GMT
What is the Physical Layer?
The physical layer refers to the method data gets from one place to another. In this case, we’re talking about transmission by air, RF. Whilst this isn’t, in some ways, as physical as a copper cable, we have to remember that, at a basic level, communication is about making a high voltage in place A change the voltage in place B. The message physically moves from A to B and the medium it uses and the way it manipulates that medium are what we refer to as the physical layer.
In this webinar, Luke will talk about System Discovery and Signalling, defined by document A/321 and the Physical Layer Protocol defined by A/322. Both freely available from the ATSC website. The webinar will finish with a Q&A. Let’s take a deeper look at some of the topics which will be covered.
Choice of modulation
ATSC 3.0 has chosen the COFDM modulation scheme over the previous 8VSB, currently used for first-generation ATSC broadcasts, to deliver data over the air from the transmitter. COFDM, stands for Coded Orthogonal Frequency Devision Multiplexing and has become the go-to modulation method for digital transmissions including for DAB, DAB+ and the DVB terrestrial, satellite and cable standards.
One of the reasons for its wide adoption is that COFDM has guard bands; times when the transmitter is guaranteed not to send any data. This allows the receiver some time to receive any data which comes in late due to multi-path reflections or any other reason. This means that for COFDM, you get better performance if you run a network of nearby transmitters on the same frequency – known as a Single Frequency Network (SFN). A transmitters signal from further away will arrive later, and if in the guard interval, will be used to re-inforce the directly received signal. This means that, counter-intuitively from analogue days, running an SFN actually helps improve reception.
Multiple operating points to match the business case
Another important feature of ATSC 3.0 at the physical layer is the ability to be able to choose the robustness of the signal and have multiple transmissions simultaneously using different levels of robustness. These multiple transmissions are called pipes. As many of us will be familiar with, when transmitting a high bandwidth, the signal can be fragile and easily corrupted by interference. Putting resilience into the signal uses up bandwidth either due using some of the capacity to put error checking and error recovery data in or just by slowing down the rate the signal is sent which, of course, means not as many bits can be sent in the same time window.
Because bandwidth and resilience are a balancing act with each one fighting against the other, it’s important for stations to be able to choose what’s right for them and their business case. Having a high robustness signalm for penetration indoors can be very useful for targeting reception on mobile devices and ATSC 3.0 can actually achieve reception when the signal is below the noise, i.e. a negative signal to noise ratio. A higher bandwidth service delivering UHD at around 20Mbps can be achieved, however, by using 64 instead of 16 QAM.
Register now!
Speaker

|
Luke Fay
Chairman, ATSC Technology Group 3,
Senior Manager Technical Standards, Sony Home Entertainment & Sound Products – America
|